SSL Enabled Plastic Connections - Reborn!
NOTE: This article is updated and maintained at this link hereHere are the instructions on how to configure Plastic SCM release 3.0.187.x
(x > 0) to communicate using a secure SSL channel between the client and server.
First download and unzip the following package. PlasticSCM_SSL_ConfigFiles.zip. Next we are going to copy these files to specific locations.
Server setup:
- Stop the Plastic SCM server service from windows services
- In Windows goto Start->Run->type "services.msc" and find the Plastic Server service and stop it.
- Navigate to your Plastic SCM server installation folder and rename your current remoting.conf file to remoting.conf.bck.
- From the zip file server folder extract the new remoting.conf to the Plastic server installation folder.
- The provided remoting.conf file will configure your server to use the default TCP port 8084 for non-SSL client connections and TCP port 8085 for SSL connections.
- You can change the Listening ports above by editing the remoting.conf file.
- A plastic.key and a plastic.cert files should be generated for the SSL to work, these files should be placed in the Plastic SCM server folder.
- to generate the files, we will use a certificate generator tool makecert.exe obtainable from the .NET SDK:
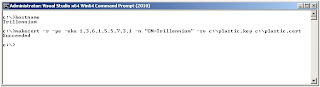
http://msdn.microsoft.com/en-us/library/bfsktky3%28VS.80%29.aspx - use the following command from within .NET SDK command Prompt: c:\>hostname
- record the above hostname to use it in the following command to generate the certification files:
- c:\> makecert -r -pe -eku 1.3.6.1.5.5.7.3.1 -n "CN=hostname" -sv c:\plastic.key c:\plastic.cert
- see Figure 1
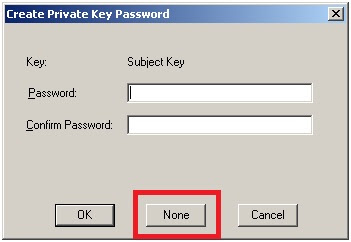
- If a pop up window “create Private Key password” is shown, choose None as illustrated in Figure 2
- Copy the generated plastic.cert and plastic.key from c:\ to the plastic scm server folder.
- Edit the remoting.conf file for the plastic server to point to the above generated certificate files; find the section and update it as illustrated below.
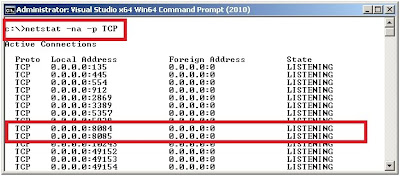
- Start the Plastic server, and check the connections on the server machine to verify that server is listening on the right TCP ports, executing the following command from a command-prompt c:\>netstat –na –p TCP as illustrated on Figure 3
<channel type="Codice.Channels.PlasticSecuredTcpChannel,
plastictcpchannel" port="8087"
sslCertificateFile="C:\Program files\PlasticSCM\server\plastic.cert"
sslPrivateKeyFile="C:\Program files\PlasticSCM\server\plastic.key";
name="secured">
Client setup:
To enable the Plastic SCM client to connect to the Plastic SCM server using SSL, first extract from client folder within the zip file, the file remoting.conf that should be extracted and placed in the Plastic SCM client installation folder.
Complete the setup following the below steps:
- re-run the Client configuration wizard, and point to the port that is used for SSL, in our case port 8085.
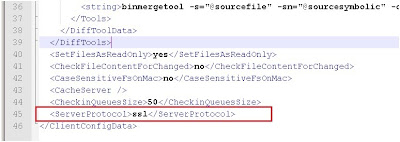
- edit the client.conf file adding the following line:
- <ServerProtocol>ssl</ServerProtocol>
- see Figure 4
- if you want to use the previous non SSL connection, you must remove the above added line in the client.conf file and re-run the Client configuration wizard, and point to the port that is used for non-SSL connections, in the default case port 8084.
The makecert.exe program is part of the Windows SDK, so Windows developers probably already have it. We found some easy instructions on doing this on another blog post here.


Ouch! Too much work... if using custom certs this should be setup straight out of the box.
ReplyDelete:)
ReplyDeleteRight, you're right, but let us go step by step... We'll include it in the setup process soon...
Great topic choose by you.
ReplyDeleteBut Too abundant work. I would like to know full setup guideline.
Before couple of day i install my UCC certificate form clickssl.com
Hm, interesting. Is it possible to use replication over SSL?
ReplyDeleteWell, at the time answering this we already have it running with an internal build that hopefully soon will be released, I tested it and now it does replication over SSL :) so there is indeed something to look forward too in one of the coming releases.
ReplyDeletecheers,